
OpsCentre is Partnering with Sterling to Support Business Resilience in Australia
Staying in compliance with Australia’s background screening regulatory requirements can

Staying in compliance with Australia’s background screening regulatory requirements can

In the wake of the global Covid-19 pandemic, businesses worldwide

In today’s digital landscape, protecting sensitive information and safeguarding against

More moving parts mean more chance of failure. Replace “moving

Most businesses experience change constantly. Markets, technologies, regulations and strategies

It may sound strange to talk about “touchy-feely” stuff like
Few activities and operations are truly set it and forget

Do more with less. Who hasn’t already heard that in

More moving parts mean more chance of failure. Replace “moving parts” by “comatose IT servers” and the adage still holds true.

The enemy is (largely) within, when it comes to the security of information and information systems. Knowing how and why insider threats materialise is a big step towards dealing with them.

Most businesses experience change constantly. Markets, technologies, regulations and strategies all evolve. Enterprises that stand still get left behind and disappear, one way or another.

Proverbially at least, elephants never forget. Neither does the Internet. Once information is out there, you must assume it will always be out there, and that deleting it at its source may make no difference.
Few activities and operations are truly set it and forget it. Lights-out factories like the showcase installation run by technology company Siemens are proof of concept, but still the exception.

Do more with less. Who hasn’t already heard that in business? And just because something – like disaster recovery planning and management – is vital to ensuring enterprise survival does not mean that you cannot leverage your investment to get more out of it.

It may sound strange to talk about “touchy-feely” stuff like user experience in the context of IT disaster recovery. After all, the priority is on getting systems up and running again within recovery time and recovery point objectives, rather than sitting around in focus groups discussing feelings and opinions.

IT service management changed a few years ago with the introduction of containers. They helped usher in the concept that a data centre was no longer a place with computers, but that the data centre itself was the computer.

Time is money, as they say, and it is also a key factor in IT disaster recovery. Take, for instance, the well-known recovery time objective or RTO, which defines how fast you should get back to normal operations after an IT incident.

Imagine taking your car to the garage for an urgent repair, only to be told that you’ll have to wait for week because the garage mechanics are off on a training course.

Military precision? Business descriptions? No fluff? All these qualifications have a bearing on a disaster recovery plan, but with certain conditions.

We may live in a digital age, but much of the concepts from the previous industrial era still carries through. We have virtual cloud data factories and production lines, just like their physical counterparts for making cars, furniture, aircraft and so on.
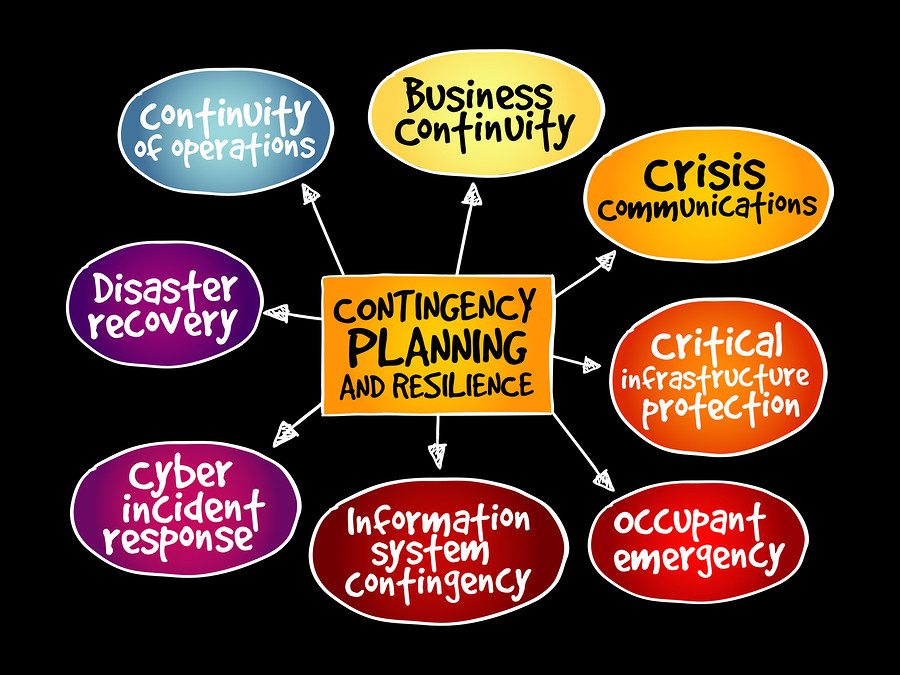
The bigger an organisation gets, the more the plans multiply. There may be plans for dealing with contingencies, crises, disasters, emergencies, pandemics, risks and who knows what else, all in addition to your business continuity plan.

It’s commonplace to see articles and discussions about cyber security and the law, but this article is not about that. It is about cyber security and law firms, those august institutions with their lawyers, barristers, and attorneys.
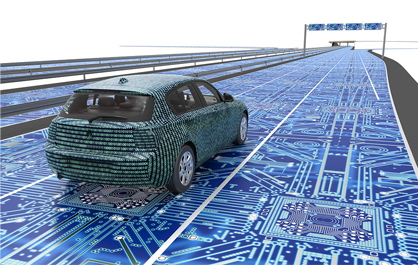
Artificial intelligence is finding its way into many applications and systems, so why not disaster recovery? The advantages are multiple.

The Agung volcano in Indonesia has been in the news recently. At time of writing, observers are sending back reports of clouds and glows that suggest that major eruption could be imminent.
When hackers try to penetrate your databases and IT infrastructure (or perpetrate any other cybercrime), they often plan a sequence of steps to get what they want. Individual steps may seem innocent or meaningless.
Much of business continuity today can be automated. Production lines, supplies reordering, failovers in case of problems, management reports, many of these things now work on a “set it and forget it” basis.

Linux has an enviable reputation as a secure platform for servers. But Linux the Unhackable? Certain myths persist about the inherent resistance of Linux to viruses and the superfluity of firewalls.

Business continuity is good for your business, but is it also a legal requirement? Laws and regulations differ from one country or one industry to another, although there is a basic expectation that organisations will act responsibly.
Get Started
For urgent inquiries, call us on 1300-BCPLAN (Intl. +612 9098 9000)



As an executive in any business, it is understandable that you want to ensure it is 100% safe, because your business is only as strong as its weakest link.
+612 9098 9000
subscribe our newsletter go get the latest updates and news from Opscentre
Copyrights © 2024 OpsCentre | Powered by PixxelStudio86.