
The Most Worrying Definition of the Blended Attack
It almost seems that there are as many definitions of the “blended attack” in IT security, as there are experts willing to give them.

It almost seems that there are as many definitions of the “blended attack” in IT security, as there are experts willing to give them.

Ideally, business continuity means no discontinuity.

Once upon a time, IT security was all about building the highest wall possible to keep attackers out and corporate users and systems safe.

In theory, IT should be a boon for business continuity. Speed, reliability, automation, efficiency, productivity, all these things are positive effects available by moving to a digital environment driven by information technology.

Risk assessment is already a vast subject and the pitfalls of risk assessment alone would probably fill a good-sized book.

Politics in career progression, in investments, in enterprise projects – but in business continuity as well?
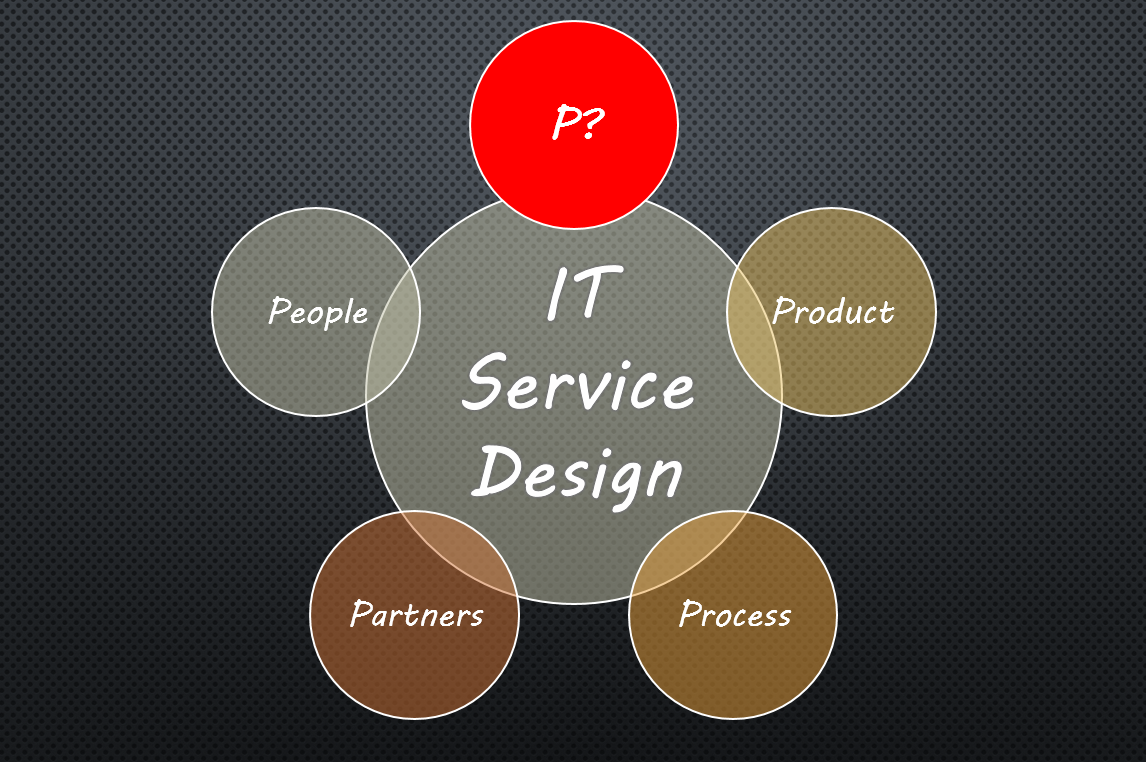
People, products, processes, and partners are the four “P”s of IT service design in a lifecycle model for IT services, but is there something missing?

To stay healthy, should you get your jabs or eat your vegetables?

Back in 2004 at the RSA Security Conference, Bill Gates was campaigning for the replacement of the password by two-factor authentication or some other secure mechanism.

Don’t get us wrong, simply telling somebody how wonderful he or she is unlikely to guarantee business continuity!

Talk about the long arm of the law!

In business continuity management, should you start with what you want or with what you have?

The case of Code Spaces still echoes in cyberspace.

Did you know that car manufacturers tend to choose the letters for their car model references according to the type of buyer they want to attract?

Tougher to do, and with tougher consequences if you get it wrong: these are the two big trends in IT risk management today.

Ah yes, agile, that buzzword that is being borrowed by so many parts of businesses! The word itself is full of promise, suggesting all kinds of good things, like flexibility, nimbleness, and adaptability.

We’d be straining your patience if we didn’t explain the title of this blog right away. ITSM?

Jargon crops up everywhere, and business continuity is no exception. RTO, RPO, BIA, and others are often sprinkled liberally into conversations, plans, and reports.

Attack sophistication is growing. 20 years ago, social engineering had already made inroads and automated attacks were on the rise, with denial-of-service, browser executable attacks, and techniques for uncovering vulnerabilities in the binary code of applications.

Every so often it’s good to shake things up. Sometimes the simple act of asking questions about what we do in business continuity and why we do it can give us a fresh point of view and point out areas for improvement.

Governments often make legal requirements about things that could damage people’s health, whether in a physical, financial, or possibly other sense.

The cliché of “change is the only constant” is true for most enterprises. Customers, business analysts, and employees all expect some sort of evolution, even if it is with varying degrees of enthusiasm.

If confidential information didn’t exist, you wouldn’t have to worry about data breaches.

Now that so many people and enterprises have rushed headlong into mobile, cloud, or both, it’s time to take a step back and consider your security posture relating to these two items.

What does a perfect storm make you think of – natural catastrophes, perhaps, like the one portrayed in the film “The Perfect Storm”, the risks confronting the Korean economy, or simply a situation you would rather avoid in the interests of business continuity?

IT service management is sometimes described as a customer-focused approach to making information technology available.

According to certain industry analysts and software vendors, we are now midway between a stage 10 years ago when few applications used machine learning, and a stage 10 years into the future when apparently, most applications will function with it.

Labour-saving devices, robots, and automation – Weren’t they all supposed to improve the quality of life, by removing manual work and drudgery?

If you thought virtual reality (VR) and augmented reality (AR) were just gimmicks for people with too much time on their hands, you could be in for a surprise.

Some IT security attacks start from the most innocent mobile apps and in ways that let cyber-criminals simply pick up confidential communications without having to hack into anything at all.
Get Started
For urgent inquiries, call us on 1300-BCPLAN (Intl. +612 9098 9000)



As an executive in any business, it is understandable that you want to ensure it is 100% safe, because your business is only as strong as its weakest link.
+612 9098 9000
subscribe our newsletter go get the latest updates and news from Opscentre
Copyrights © 2024 OpsCentre | Powered by PixxelStudio86.