
Cyber Security and Pointers from Criminology
While cyber security may have you thinking in zeros and ones, and wondering which next generation firewall you should buy next, the human element is alive and well in cyber crime.

While cyber security may have you thinking in zeros and ones, and wondering which next generation firewall you should buy next, the human element is alive and well in cyber crime.

If everything is working and you have a business continuity plan in place, is there anything left to worry about? Yes!

With the aim of IT service management being to serve the business or the organisation funding the IT, it’s crucial that business requirements drive ITSM projects and procurement.
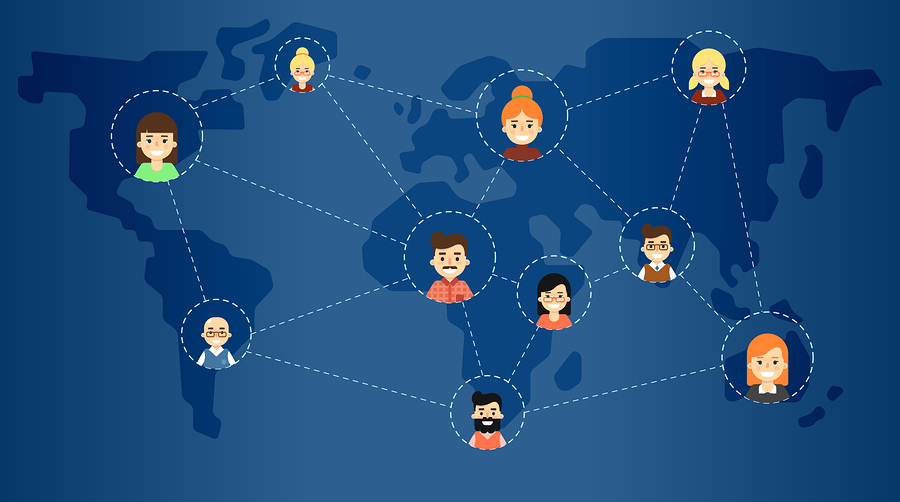
The “six degrees” concept is that you can reach any person in the world using a maximum of six personal relationships in a chain stretching from you to the person you want to reach.

In principle, every IT system needs to be secure. In practice, some IT systems are less secure than others.

So, it’s that time of the year again, when we look back over the last 12 months in business continuity to see… nothing?

Does Father Christmas know just how exposed his operation is? With one of the largest address books ever conceived (names, addresses, gift preferences of billions of people) and a seasonal workforce of elves that may or may not have been vetted before hiring, Santa’s gift selection, preparation and delivery system may be hugely at risk.

Meet Sophia, who has Saudi-Arabian nationality. There’s nothing unusual about that, except that Sophia is a robot.

The idea behind threat hunting is that some attackers are getting too smart for current IT security technology.

In theory, IT service management should contain sprawl, limiting or preventing the spread of underutilised IT assets.

“Yes, we have a business continuity plan”. Every enterprise wants to hear this from its suppliers, especially the key suppliers.

First, there was the virtual machine. Then came the container. Now, welcome to the unikernel, the latest initiative for atomising computing.

Fear, uncertainty and doubt. Collectively known as FUD, these items skew rational thinking, panic otherwise sensible people, and throw sizeable spanners in the works of business continuity planners.

Will it ever go away? The basic password is still alive and well.

Bankruptcy per se is not necessarily the end of an enterprise, as several high-profile phoenixes rising from the ashes have shown.

It’s not paranoia, they really are out to get you. When the very organisations promoting IT security manage to botch it up, it’s difficult to have confidence in anything anymore.

You may well have heard the story of the person trying to streamline business operations and driving past huge, separated grain silos one day, which reminded him of the mentalities and divisions he was trying to overcome back in the office.

It’s a fact of business life that customers, markets, and industry commentators only see your brand, and not the suppliers who provide the materials, components, or products behind it.

People – “Can’t live with them, can’t live without them” might be the motto for many enterprises and their chief information security officers (CISOs).

Sometimes in business continuity we end up with such a fierce focus on actions inside the enterprise that we neglect actions directed towards the outside world, and specifically towards our customers.

Hollywood (once again) got there first. Remember those films in which shadowy figures hiss “Trust no-one!” before vanishing from the scene?
You may find this blog article mind-expanding – especially if your natural reaction is to think about its title in two dimensions, rather than three. To set things straight, we’re not talking about paper printouts of business continuity plans that by definition are out of date the moment they are distributed.

What’s more important in IT Service Management (ITSM), the management or the service?

When you look at something, you have an impact on it. That’s the observer effect.

If you’ve worked in IT development for hardware or software, or had dealings with that world, you may well have seen the statistics about the costs of fixing bugs.
How many times have you heard business people talk about their DNA – meaning their business culture or something similar?

What’s the difference between a risk, a threat, and a vulnerability? This is worth knowing, because if you can spot the risks in your enterprise and mitigate or eliminate them, you might not have to worry about associated threats.

As a business continuity manager, you are likely to be involved in getting your colleagues to take business continuity seriously and ensure that their own departments will continue to function even in adverse conditions.

It’s always good to show how business continuity can be a net profit generator or produce other positive and measurable advantages.

Sounds obvious? When you’re knee deep in metrics, reports, and audits, it’s not always easy to remember that without people doing their jobs, nearly every organisation will rapidly cease to function.
Get Started
For urgent inquiries, call us on 1300-BCPLAN (Intl. +612 9098 9000)



As an executive in any business, it is understandable that you want to ensure it is 100% safe, because your business is only as strong as its weakest link.
+612 9098 9000
subscribe our newsletter go get the latest updates and news from Opscentre
Copyrights © 2024 OpsCentre | Powered by PixxelStudio86.