Enterprise Attacks that Start in Mobile Apps

Some IT security attacks start from the most innocent mobile apps and in ways that let cyber-criminals simply pick up confidential communications without having to hack into anything at all.
Ransomware is so 2016 – The New Menace is Ransomworm

Don’t take this title too literally. Ransomware, the malware that extorts money from victims to prevent a disaster, will surely continue to be active, at least in the short term.
Will Every IT Security Risk Now Be Followed by a Fake Risk?
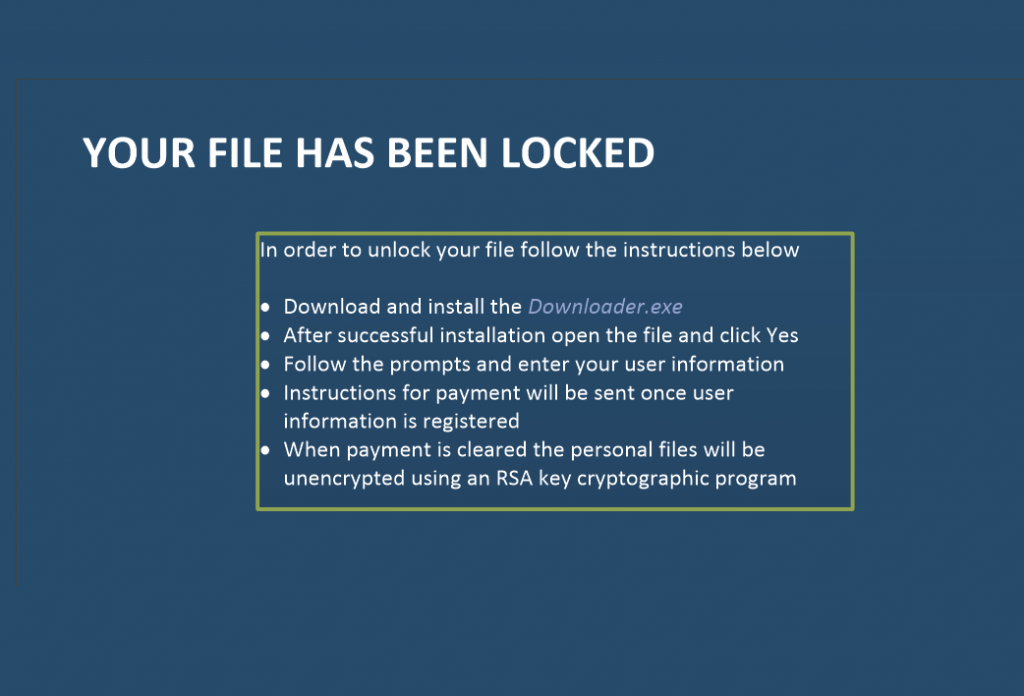
It would be risky to generalise from one specific example in IT security, but the case of fake ransomware is intriguing.
Is It Time to Review Your Malicious Software Reporting Policy?
Be honest – do you currently have a malicious software reporting policy? Just relying on the existence of anti-virus software and firewalls may be too optimistic nowadays. The potential damage to information assets and productivity, let alone identity or bank account theft, suggests that a malware reporting policy should be in place in any organisation. […]

