Business Continuity in 2017 – Lest We Forget?

So, it’s that time of the year again, when we look back over the last 12 months in business continuity to see… nothing?
The Vulgarisation of IT System Hacking Could Be Good News

Attack sophistication is growing. 20 years ago, social engineering had already made inroads and automated attacks were on the rise, with denial-of-service, browser executable attacks, and techniques for uncovering vulnerabilities in the binary code of applications.
Is It Time to Rename Malware as Sneakyware?

Malware (Sneakyware) is the software that gets into your system and causes havoc, unless you detect it and neutralize first.
Business Continuity and the Knock-On Blackouts

Power blackouts in business can range from a minor inconvenience to a major threat. Diggers slicing through power cables, extreme weather conditions bringing down power lines, or other local failures can all interrupt the supply of electricity.
Our 2016 Business Continuity Review – From National Resilience to Toasters (and Back)

It’s always an editorial dilemma – Do we start with the event with the biggest business continuity impact? The event that was the most unbelievable? For the 2016 Business Continuity Review, we have some difficult choices, including the massive cyberattack of the toasters, the most powerful man in the world (soon) trying to carve up the Internet, and a smartphone threatening the health of a national economy.
ABS Census Attacked by DDoS
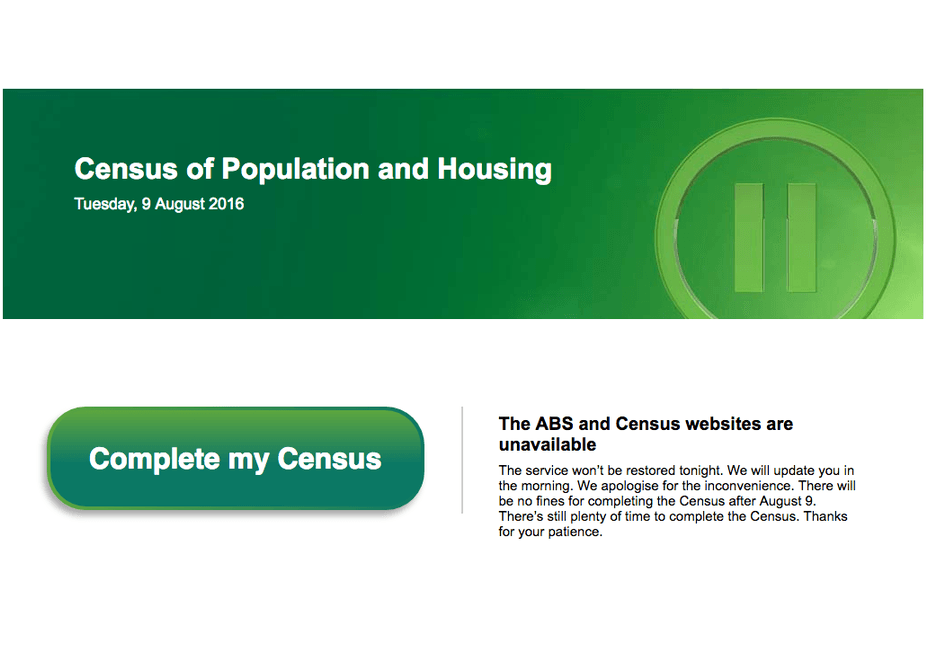
What were Australian’s doing on the evening of the 9th of August, 2016? All jumping on the bandwagon to fill out their Australian Bureau of Statistics (ABS) Census details on the Census website.

