The Business Continuity Fight of the Week: Real Clouds vs. Virtual Clouds?
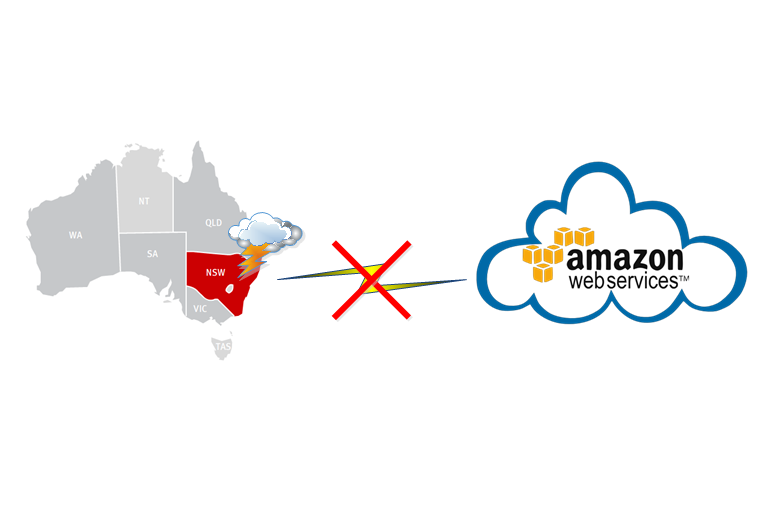
What would you expect residents of Sydney to be doing Sunday afternoon and evening, 5 June 2016?
Micro Answers to Expanding IT Security Perimeters

If you use a cloud service or let your employees access company systems from their own smartphones, you’ve probably already noticed how your IT security perimeters has expanded.
3 Broad Categories of Cyber-Security Trends for 2016
System hacks, data breaches and information theft are frequently in the news, and will surely continue to feature strongly in 2016. However, recent crystal ball gazing by different actors and experts yielded an intriguing variety of predictions for the coming year. Broadly speaking, there are IT security trends we can expect, those we should suspect, […]
Disaster Recovery Services and Multi-Tenancy in the Cloud
Historically, vendor solutions for disaster recovery have been created for on-site use for individual enterprises. The client company concerned was the sole owner of the user data involved, and disaster recovery could be implemented without having to worry about anybody else. The cloud computing model changes that situation. It’s possible to use cloud services to […]

